In today’s cloud-driven world, Software as a Service (SaaS) has become a cornerstone of business operations, offering unmatched scalability, cost-efficiency, and flexibility. From collaboration tools like Slack to CRM platforms like Salesforce, SaaS applications streamline workflows and boost productivity. However, this reliance on third-party cloud solutions introduces a host of security challenges—data breaches, unauthorized access, and phishing attacks, to name a few. For IT professionals, security managers, and business leaders, understanding these SaaS security threats and implementing effective mitigation strategies is non-negotiable to protect sensitive data and ensure compliance with regulations like GDPR, HIPAA, and CCPA.
This guide dives deep into the most pressing SaaS security threats, offering actionable insights and real-world examples to help you safeguard your organization. We’ll cover everything from access control vulnerabilities to API insecurities, vendor risks, and beyond, concluding with practical takeaways and a roadmap to strengthen your SaaS security posture. Let’s get started.
Access Control and Authentication Threats

Weak Authentication
Weak authentication remains a top vulnerability in SaaS environments. Many organizations still rely solely on username-password combinations, which are easily compromised through brute-force attacks or credential stuffing. A notable example is the 2022 Cisco breach, where attackers exploited stolen credentials to gain access, as reported by PolymerHQ. Without robust authentication, your SaaS ecosystem is an open door for attackers.
Mitigation Strategies:
- Implement Multi-Factor Authentication (MFA): Add an extra layer of security with tools like Google Authenticator or SMS codes.
- Enforce Strong Password Policies: Require complex passwords (e.g., 12+ characters, mix of letters, numbers, and symbols) and mandate regular updates.
- Use Password Managers: Encourage employees to use tools like LastPass to avoid weak or reused passwords.
Authorization Issues
Over-privileged users are another Achilles’ heel. When employees have access beyond their job requirements, it heightens the risk of data leaks—whether accidental or intentional. For instance, an employee with unnecessary admin rights could inadvertently expose sensitive customer data.
Mitigation Strategies:
- Adopt Role-Based Access Control (RBAC): Assign permissions based on job roles, limiting access to what’s essential.
- Apply the Principle of Least Privilege (PoLP): Ensure users only access the data and systems they need.
- Audit Permissions Regularly: Review access rights quarterly to revoke unnecessary privileges.
API Security Threats

Insecure APIs
APIs are the glue that connects SaaS applications, but they’re also a prime target for attackers. Insecure APIs can fall victim to exploits like SQL injection or broken authentication, leading to devastating breaches. Forbes notes that API-related attacks are surging, underscoring the urgency of securing these endpoints.
Mitigation Strategies:
- Encrypt Data in Transit: Use Transport Layer Security (TLS) to protect API communications.
- Validate Inputs: Prevent injection attacks by sanitizing all API inputs.
- Perform Penetration Testing: Regularly test APIs to uncover and patch vulnerabilities.
Data Security Threats
Data Breaches
Data breaches are a persistent threat in SaaS environments, where sensitive information resides in the cloud. Weak access controls, unpatched vulnerabilities, or insider actions can all trigger a breach, exposing customer data or intellectual property.
Mitigation Strategies:
- Encrypt Data: Use AES-256 encryption for data at rest and TLS for data in transit.
- Maintain Backups: Implement automated, encrypted backups to ensure quick recovery.
- Deploy Data Loss Prevention (DLP) Tools: Monitor and block unauthorized data transfers.
Data Leaks
Accidental data exposure—think misconfigured S3 buckets or unsecured endpoints—can lead to leaks that go undetected for weeks or months. These incidents often stem from human error rather than malicious intent.
Mitigation Strategies:
- Audit Configurations: Use tools like AWS Config to ensure permissions are locked down.
- Train Staff: Educate employees on secure data handling practices.
- Monitor Access Patterns: Deploy anomaly detection to flag unusual activity.
Data Ownership Issues
In SaaS setups, data ownership can get murky. Who controls your data—the provider or your organization? Ambiguity here can lead to compliance headaches or disputes.
Mitigation Strategies:
- Define Ownership in Contracts: Ensure SaaS agreements clarify data control and usage rights.
- Comply with Data Sovereignty Laws: Store data in regions that align with local regulations.
Data Retention Problems
Hoarding data beyond its useful life increases exposure risks. Outdated records lingering in the cloud are a liability waiting to be exploited.
Mitigation Strategies:
- Set Retention Policies: Align storage durations with regulatory requirements (e.g., GDPR’s “right to be forgotten”).
- Audit Stored Data: Routinely purge unnecessary information.
Social Engineering Threats
Phishing Attacks
Phishing is a perennial menace, especially in SaaS ecosystems. Attackers impersonate trusted services—like your HR platform—to trick users into revealing credentials or downloading malware.
Mitigation Strategies:
- Educate Employees: Conduct regular training on spotting phishing emails (e.g., suspicious links, urgent tones).
- Filter Emails: Use tools like Barracuda to block malicious messages before they reach inboxes.
- Enable MFA: Reduce the impact of stolen credentials with an additional verification step.
Vendor and Supply Chain Threats
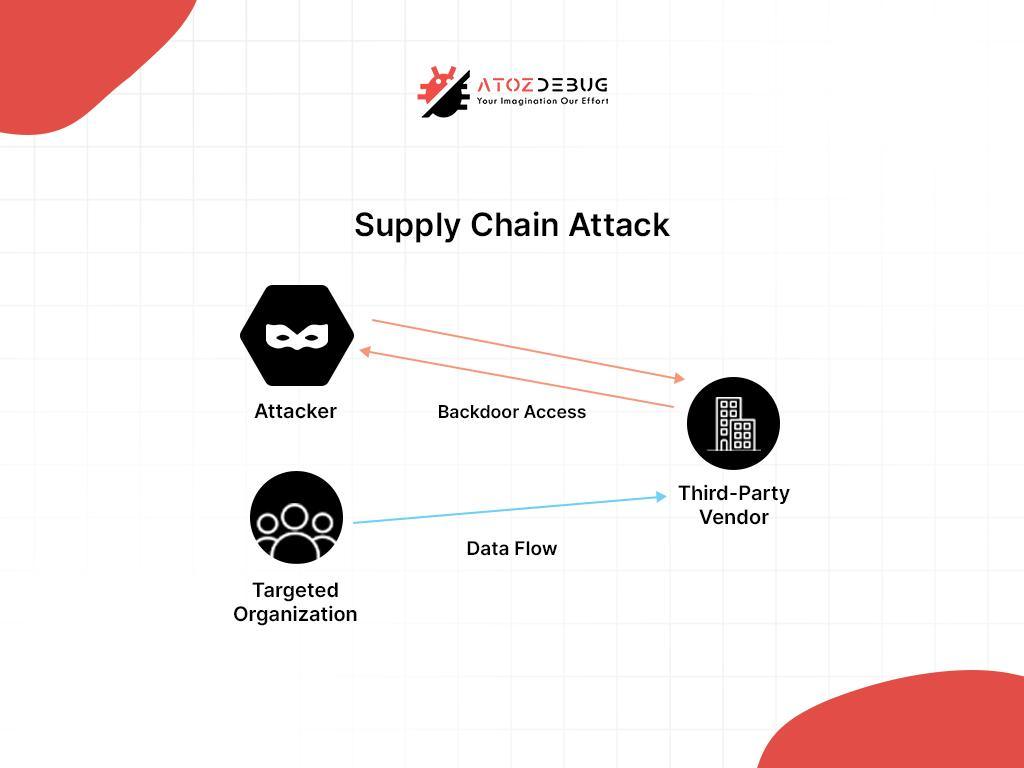
Vendor Security Breaches
Your SaaS provider’s security is your security. If a vendor gets breached, your data could be next. Third-party risks are real—just look at high-profile incidents like the SolarWinds attack.
Mitigation Strategies:
- Vet Vendors: Review certifications like SOC 2 or ISO 27001 during selection.
- Secure SLAs: Include breach notification timelines and security commitments in contracts.
- Monitor Vendors: Use tools like BitSight for ongoing risk assessment.
Supply Chain Attacks
These attacks target the software supply chain, injecting malicious code into SaaS updates before they reach you. The result? Compromised applications you thought were safe.
Mitigation Strategies:
- Demand Secure Development: Ensure vendors conduct code reviews and vulnerability scans.
- Track Updates: Monitor patch releases for anomalies using checksum verification.
Configuration and Compliance Threats
Misconfigurations
Misconfigurations—like leaving cloud storage buckets publicly accessible—are a leading cause of SaaS breaches. A single oversight can expose gigabytes of data.
Mitigation Strategies:
- Automate Audits: Use tools like CloudSploit to detect and fix misconfigurations.
- Leverage Infrastructure as Code (IaC): Enforce secure settings programmatically.
Compliance Violations
Non-compliance with regulations like GDPR or HIPAA can lead to fines and reputational damage. SaaS complexity often makes adherence tricky.
Mitigation Strategies:
- Use Compliance Tools: Platforms like Drata help track regulatory requirements.
- Conduct Audits: Regularly verify policies against standards like CCPA.
Internal Threats
Insider Threats
Insiders—whether malicious or careless—pose a unique risk. A disgruntled employee with access to sensitive SaaS tools could wreak havoc.
Mitigation Strategies:
- Monitor Behavior: Use User and Entity Behavior Analytics (UEBA) to spot anomalies.
- Separate Duties: Limit any single user’s control over critical systems.
- Train Staff: Reduce accidental threats with ongoing security awareness programs.
Malicious Software Threats
Malware
Malware can sneak into SaaS environments via phishing emails, compromised APIs, or third-party integrations, disrupting operations or stealing data.
Mitigation Strategies:
- Install Antimalware: Deploy solutions like CrowdStrike to detect and neutralize threats.
- Patch Regularly: Keep SaaS apps updated to close exploit paths.
Ransomware
Ransomware encrypts your data and demands payment, grinding business to a halt. SaaS environments aren’t immune, especially if backups are lacking.
Mitigation Strategies:
- Keep Offline Backups: Store copies disconnected from the network.
- Use EDR Tools: Endpoint Detection and Response solutions can isolate infections early.
Visibility and Control Threats
Lack of Visibility and Control
SaaS environments often leave organizations blind to user activity and data flows, complicating threat detection.
Mitigation Strategies:
- Implement SSPM: SaaS Security Posture Management tools provide configuration insights.
- Deploy CASBs: Cloud Access Security Brokers monitor and regulate data movement.
Conclusion
Securing a SaaS environment is no small feat, but it’s entirely achievable with the right approach. Threats like weak authentication, insecure APIs, vendor breaches, and insider risks are real—but so are the solutions. By enforcing MFA, securing APIs with encryption, auditing vendors, and leveraging tools like SSPM and CASBs, you can build a robust defense. The shared responsibility model is key: SaaS providers secure the infrastructure, but you’re accountable for access controls and data protection.
Don’t wait for a breach to act. Start today by auditing your SaaS security posture. Identify gaps in access management, API security, and compliance, then apply the strategies outlined here. Proactive security isn’t just a safeguard—it’s a competitive edge.